Cloud IAM is a Segura® Identity and Access Management module to control access to resources in Cloud Service Providers (CSPs).
Cloud IAM can be used to provision users and service accounts in a multi-cloud architecture. With it, administrators can monitor all cloud environments and users in a centralized and controlled way. In addition, Segura® tracks activities to ensure compliance through audit reports and session recordings.
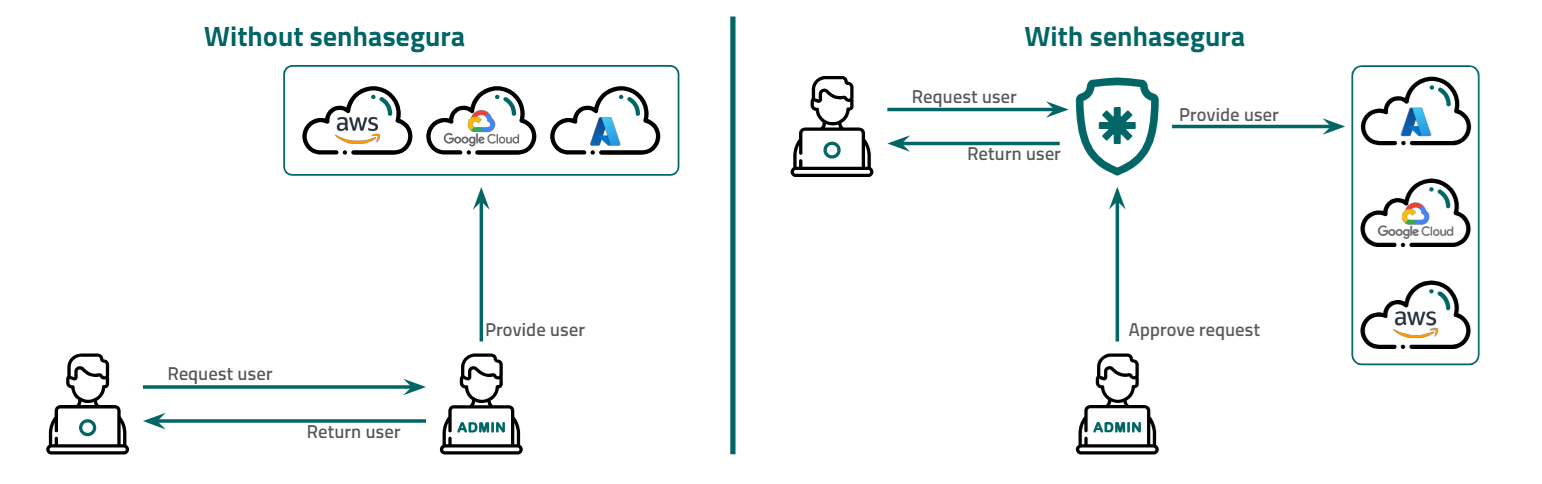
How it works
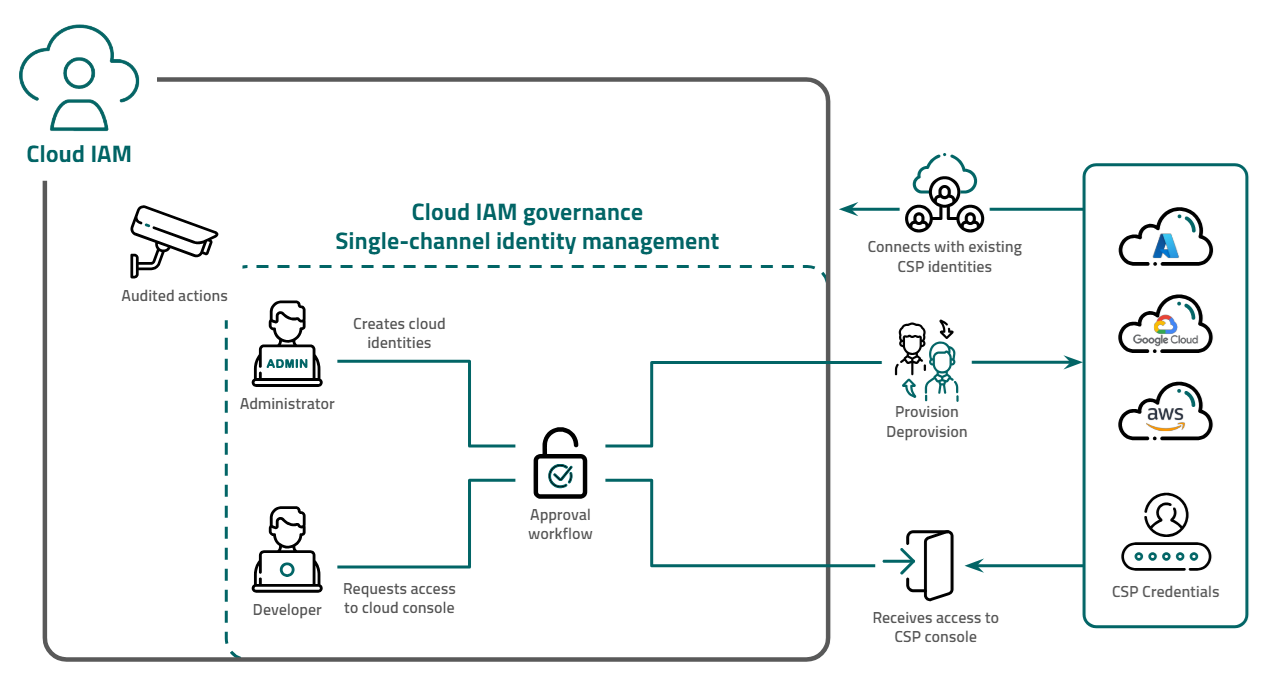
Cloud IAM allows access control to be managed across multiple CSPs through a single approval workflow. When a request is made to access a resource, the administrator receives a notification in the Cloud IAM console containing the necessary details. From the console, the administrator can create or modify users or access groups across multiple cloud providers simultaneously. This involves configuring the required permissions, roles, credentials, and access keys for the request. Once the user is provisioned, Cloud IAM receives information from the CSPs and creates auditing details for each access granted across all configured CSPs.
Features
Cloud IAM main features include:
- Centralized cross-cloud identity provisioning.
- Immediate provisioning of users, access keys, and service accounts.
- Creation of templates. These templates create a standard mask for creating new users and service accounts.
- Dynamic provisioning of policies, roles, resources, and permissions through the Devops Secret Manager.
- Provisioning of Just-In-Time (JIT) credentials and JIT access control.
- Recorded remote sessions of the AWS cloud console.
- Management of access requests and access groups.
- Audit tracking reports.
Applicability
Cloud IAM is applicable whenever an organization needs to go beyond the basic capabilities of native CSP IAM systems to implement robust, centralized, policy-driven, and auditable management of their most privileged cloud identities and access. It helps bridge the gap between native cloud security features and Privileged Access Management (PAM) requirements. This approach helps organizations manage the complexity of privileged access in multi-cloud or hybrid cloud environments, enhance security by removing standing privileges, meet compliance requirements, and gain greater visibility and control over their most critical cloud accounts and resources.
Cloud IAM currently supports the following providers: