- 1 minute to read
- Print
- DarkLight
- PDF
Discovery logs
- 1 minute to read
- Print
- DarkLight
- PDF
Through the Discovery module, you can view a series of reports such as Device Discovery logs, Credential Scan logs, Discoveries status, pooled connections, and a list of unauthorized access to devices registered in the vault.
To view discovery logs, go to Discovery ➔ Logs ➔ Device Discovery Logs
Synchronize
In the Report Action button, click Synchronize.
When synchronized, a success message will be shown.
Visualize Discovery Logs
Access the Discovery menu ➔ Logs ➔ Connections by device, and on the log action button, click View Discovery Logs.
Discovery Logs
Through the Discovery module, you can view a series of reports such as device:
- Discoveries logs
- Credential scans logs
- Discoveries status
- Pooled connections
- List of unauthorized access to devices registered in the vault.
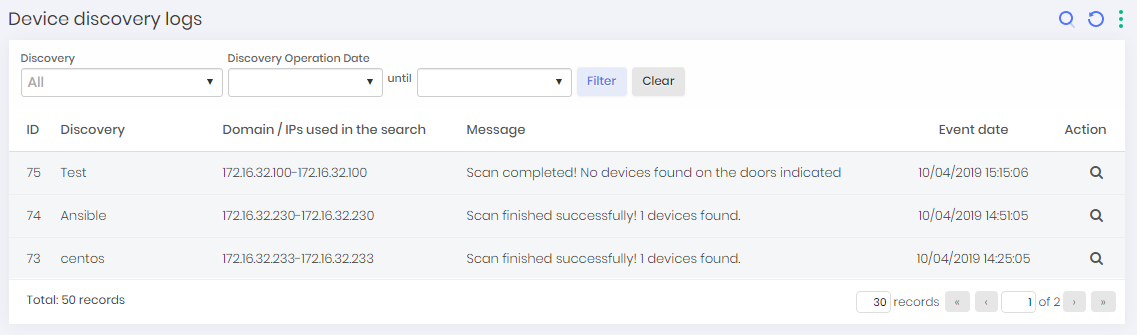
To view the discovery logs, go to Discovery ➔ Logs ➔ Device Discovery Logs
On this screen, you can view device discoveries logs along with a range of information such as Discovery name, search range, message, and date of occurrence.
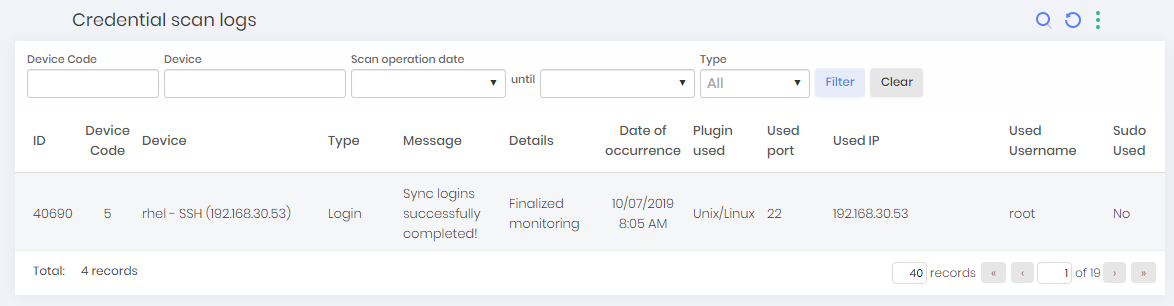
Credential scan logs
To view credential scan logs, go to Discovery ➔ Logs ➔ Credential Scan Logs
In this screen, you can view the credential Scan logs along with a series of information such as device, message, date of occurrence and username used.
Details of pool connections by device
To view details of device pool connections, go to Discovery ➔ Logs ➔ Credentials
You can view Discoveries configured using device-separated credential pools along with management IP, device name, and Discovery status on this screen.
Details of pool connections by credentials
To view details of pool connections by credentials, go to Discovery ➔ Logs ➔ Device Connections Credential Devices.
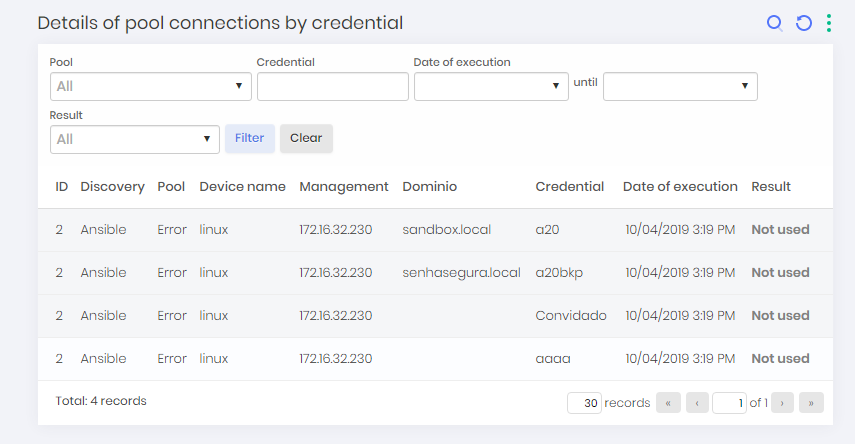
In this screen, you can view Discoveries configured using credential-separated credentials pools along with management IP, device name, pool name, date of execution, and Discovery result.
Report of certificates with import error
In this report, you will present the certificates with import errors during the Discovery. The report also includes a column highlighting the certificates that were not imported because they have a password or key.
Access the report along the way: Discovery ➔ Discovery ➔ Certificates ➔ Certificates with password

