GitHub is a widely used platform for hosting source code and files. It provides Git-based version control, allowing programmers, utilities, and users to contribute to private and open source projects, regardless of location. GitHub Actions is a powerful tool that enables the automation, customization, and execution of development workflows directly in the repositories. This integrated functionality significantly improves the efficiency and consistency of the software development process.
By integrating Segura® DSM with GitHub Actions, all environment variables can be intercepted and secrets can be injected directly into pipelines during automation execution. This approach eliminates the need to expose secrets, reinforcing security during development.
The image below shows a diagram of how Segura® DSM and GitHub Actions are integrated:
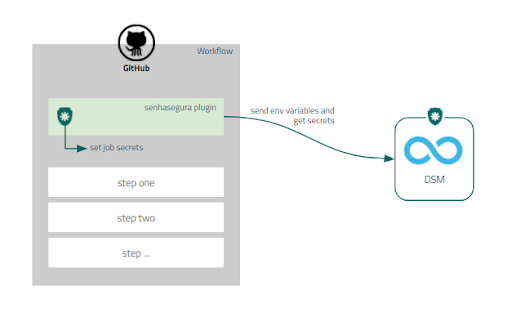
Integrate DSM with GitHub Actions
To integrate Segura® DSM with GitHub Actions, using the DSM CLI, follow the instructions below:
- Access a project from your GitHub account.
- Add the executable, the configuration file, and, optionally, the
segura-mapping.jsonfile to the project's repository. - In Segura®, access your project's CI/CD Variables by Products Menu > DevOps Secret Manager > CI/CD > Variables.
- Register the variables needed to run the DSM using CLI.
- Edit your
.github/workflows/pipeline.ymlfile in your project folder. - During the desired work of your pipeline, add the code to run the DSM and confirm the change to the file.
- Run the GitHub pipeline to finish.
If you don't have the dsm-cli and segura-mapping.json files, ask the Segura® support team for them.
Example for .github/workflows/pipeline.yaml file for using with DSM CLI:
name: Segura CLI CI/CD
on:
push:
branches: [ main ]
workflow_dispatch:
jobs:
build:
runs-on: self-hosted
steps:
- uses: actions/checkout@v2
- name: Run DSM CLI as Running Belt
env:
APPLICATION: ${{ secrets.APPLICATION }}
SYSTEM: ${{ secrets.SYSTEM }}
ENVIRONMENT: ${{ secrets.ENVIRONMENT }}
run: |
dsm runb \
--app-name $APPLICATION \
--system $SYSTEM \
--environment $ENVIRONMENT \
--config .config.yml \
--tool-name github \
source .runb.vars && rm .runb.vars
Ensure you select OAuth 2.0 as the authentication method in Segura® DSM, as the CLI uses it to fetch information.
Use DSM and CLI to inject secrets into pipelines
After configuring the DSM CLI in the project, go to the Actions menu on GitHub to run the pipeline and inject the secrets. To do this, follow the instructions below:
- Select the workflow and the Run workflow option.
- Choose the branch to run the workflow and click on Run workflow.
- Finally, click on Workflow > Job to display the result of the run.
Example of an output from the GitHub Actions workflow:
Run chmod +x senseg-cli
Using config file: .config.yml
Registering Application on DevSecOps
Trying to authenticate on Segura DevSecOps API
Authenticated successfully
Application register success
Posting variables in Segura...
Trying to authenticate on Segura DevSecOps API
Authenticated successfully
Posting variables successfully
Finding secrets from application
Trying to authenticate on Segura DevSecOps API
Authenticated successfully
Injecting secrets!
Injecting secret: Segura APPLICATION... Sucess
Injecting secret: Segura ENVIRONMENT... Sucess
Injecting secret: Segura SYSTEM... Sucess
Secrets injected!
Deleting github variables...
The config GITLAB ACCESS TOKEN is empty
Deletion failed
To delete github variables, you need to define the configs GITLAB ACCESS TOKEN, CI API V4 URL and CI PROJECT TD
Finish
Do you still have questions? Reach out to the Segura Community.