The Segura® Network Connector enables users to initiate sessions on devices located in networks without connectivity to Segura® Platform, or in environments with overlapping IP addresses.
In addition, Network Connector supports all connection types available in Segura® Platform, including RDP, SSH, Telnet, HTTP/HTTPS, and others.
This solution is composed of the Network Connector Server and the Agent.
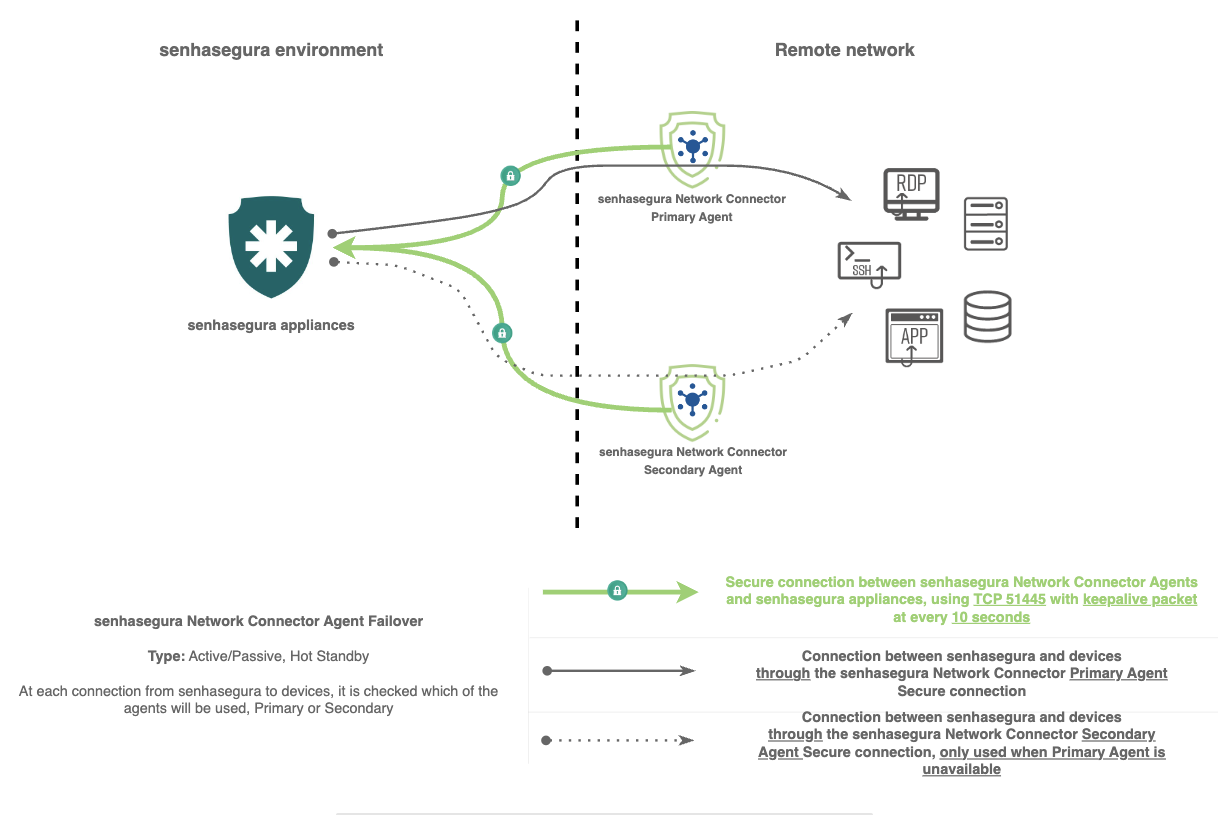
The device that has the agent installed must be able to see the Segura® Platform for the connection to be made.
When modifying the destination of the request for a tunnel established by the agent, Network Connector becomes incompatible with the use of certificates. This is because, in this context, certificates depend on the destination of the request to perform one of the necessary validations.